About

Who is Soterion?


CUSTOMERS

TEAM MEMBERS

SOLUTIONS

PARTNERS

EST YEARS AGO
Our Holistic GRC Offering
Our Approach to GRC
The threat of economic crime is a very real concern for all organisations, regardless of their size, sector or region. SAP security and Governance Risk and Compliance activities are technical and complex components of SAP, resulting often in a lack of business buy-in and accountability from management and the organisation’s business users, which diminishes the company’s GRC capability.
Access risk is business risk. At Soterion we believe that effective GRC is measured by how well the business users can carry out their access risk management activities. Soterion’s Effective GRC Pyramid illustrates the inter-relationship between the various components of SAP security and GRC. Deficiencies in any layer can negatively impact the organisation’s ability to manage their access risk.
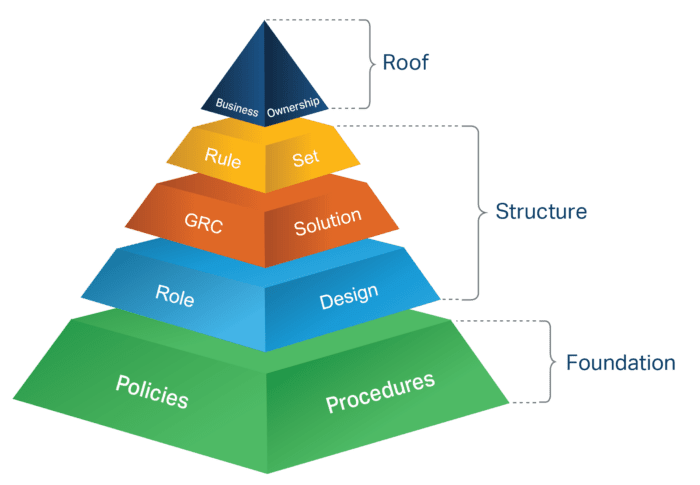
Policies and Procedures
Well defined and documented Policies and Procedures form the foundation of SAP security and GRC. Without detailed Policies and Procedures, access risk management activities are performed with minimal understanding and intent which diminishes the organisation’s GRC capability.
Role Design
The SAP role design is a crucial component of ensuring effective GRC. An inappropriate role design will result in added complexity to many of the access risk management activities, frustrating business users in their compliance tasks and hindering business buy-in and accountability.
GRC Solution
The GRC solution needs to be user-friendly for the security administrators to ensure that the SAP Security / Authorisation solution provides appropriate access. It also needs to be business- friendly (i.e. convert the technical GRC language into the language the business users can understand) to enhance business buy-in and accountability.
Rule Set
It is crucial that the organisation’s rule set contains risks that are relevant and appropriate to the organisation. Deficiencies in the rule set will result in the organisation not monitoring relevant or critical risks which could lead to fraud.
Business Ownership
Access Risk is business risk, yet in many cases this responsibility resides with the IT teams. Organisations need to implement the correct solutions and processes to obtain the appropriate level of business ownership and accountability of access risk for better decision making and effective access risk management.







