Three Benefits of Regular SAP Access Risk Assessments
For those organisations who do not have an access control / GRC solution, there are considerable benefits in performing regular SAP access risk assessments.
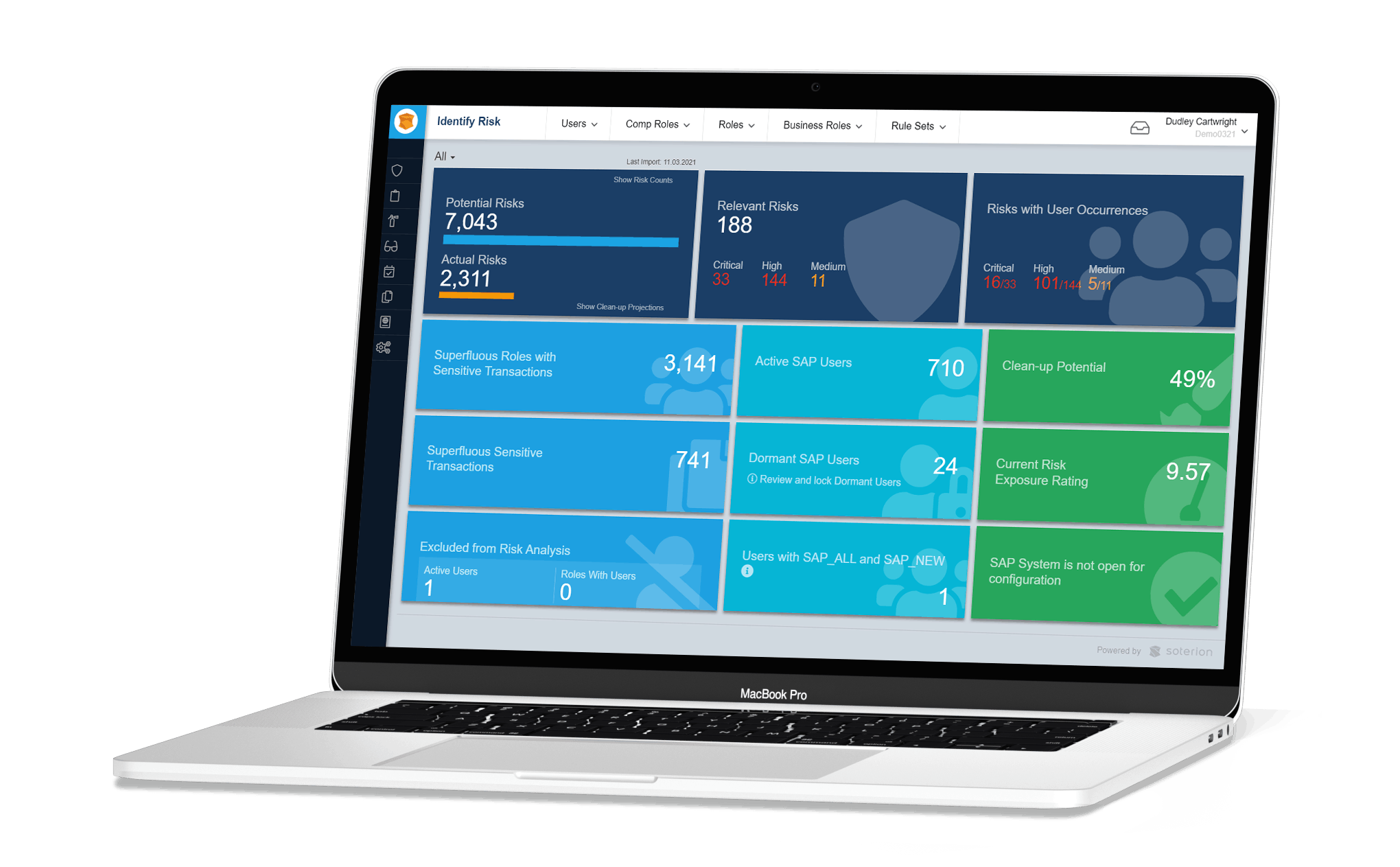
Soterion Dashboard
The appropriateness of an SAP authorisation solution degrades over time, primarily due to SAP authorisation creep. Authorisation Creep is where users inherit more access over a given period than the access removed from them as they move to different job positions internally. This also happens when they require a single transaction code but are assigned a role with many transaction codes.
Technical mistakes in the role-build process can also cause the SAP authorisation solution to provide users with wider access than required. A very basic example here is where S_TCODE is maintained in a role with S_ALR*.
It is important to note that not all S_ALR* are Display Transactions.
Another common mistake is where display roles are created with update transaction codes in them, and the ACTVT values are maintained to Display only (03, 08 etc). These roles work well in isolation, but as soon as they are assigned to users who also have other update roles, the combination of the S_TCODE value from the Display role, and the update ACTVT fields in the user’s other roles, results in the user having far wider access than intended.
It is not only unfair on the SAP security team, but also impractical, for them to pick up on these types of issues. The complexity of SAP authorisations not only means that these types of mistakes are relatively common, but the sheer volume of data makes it very difficult to identify these issues. It is like finding a needle in a haystack.
For many organisations, their external audit is the only time in the year where an access risk assessment is performed on their SAP system. These organisation have very little visibility into their SAP access risk exposure for the majority of the year, placing them at unnecessary risk.
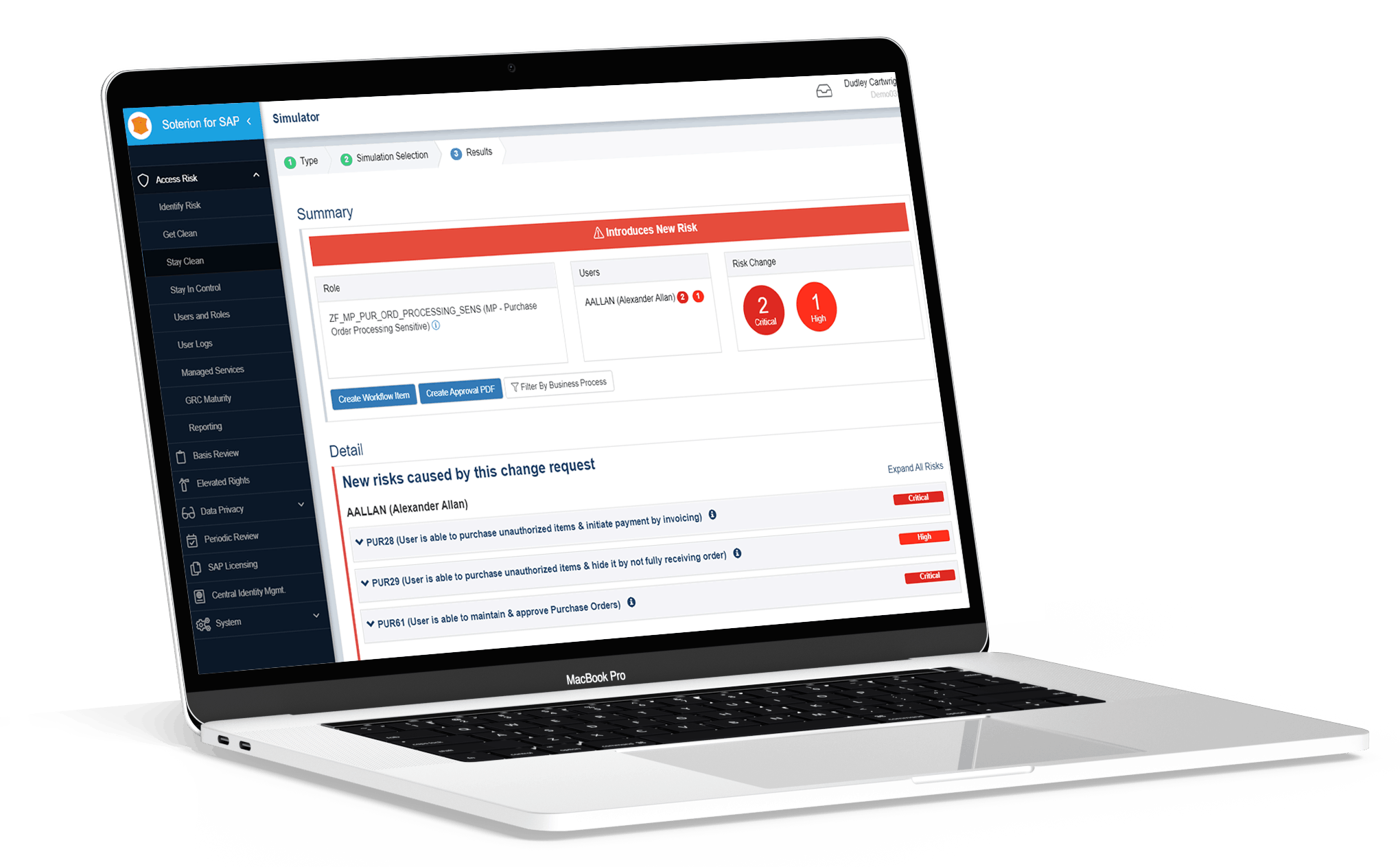
Soterion SAP Access Change Request Simulation
With a number of vendors who have developed a cloud offering, performing an access risk assessment is simple and easy. The data extraction can typically be done in less than an hour, which is the only effort required by the company. The vendor will perform the assessment and send the company their access risk results.
Performing more regular access risk assessments can be a more failsafe way to ensure the SAP authorisation solution has not provided in-appropriate access to the users during the course of the year.
Below are three benefits of performing regular SAP access risk assessments:
- Reduce SAP access risk: By performing SAP access risk assessments, you will be able to identify any role(s) that is providing users with in-appropriate access. Often it is only a handful of roles that have been incorrectly maintained that are responsible for the majority of the access risks. In many cases, these roles can be addressed with minimal effort. They are the ‘low hanging fruit’, and with minimal effort can have a significant reduction in the total access risk count.
- Better prepared for audits: Performing an access risk assessment prior to your external audit can allow you the opportunity to identify ‘quick wins’ which can be addressed prior to the audit. There is no organisation that wants an unfavourable audit report, so reducing any findings prior to audit can be quite attractive. In addition, there could be a cost-saving to being better prepared for audit. If an authorisation solution is providing users with such wide access that the audit firm believes that substantive audit procedures are required, not only will there be additional audit cost to carry this out, but there will be additional effort required by key employees to prepare for the audit.
- Enhanced business-accountability of access risk: Although access risk is business risk, the business users are unlikely to take accountability without some form of visibility i.e. you cannot be accountable for something you are not aware of. Without regular access risk assessments, the business users are unlikely to know who has access to specific SAP functions. By performing regular assessments, IT is providing the business with the necessary visibility for them to understand the access risks that exist in the SAP system. This in turn will allow IT to shift responsibility to the business. Visibility enhances accountability.
Consider how your data will be handled by the vendor performing the access risk assessment, ensure that the vendor is both ISO27001 and SOC certified. Vendors providing such services need to illustrate that they will handle client data that is in accordance with your organisation’s internal requirements as well as any regulatory requirements.
Soterion SAP Access Risk Assessment
Soterion can be used to perform an SAP access risk assessments on the organisation’s SAP environment by, either using the Soterion standard rule set, or the customer is able to import or customise their own rule set. Soterion’s SAP access risk assessment includes:
- SAP Access Risk Assessment:An access risk assessment is performed at User, Composite Role and Single Role level. Access risks reports are based on what access has been assigned (potential) and displays this in relation to the actual transaction usage. Soterion’s Get Clean module supports risk remediation consulting projects.
- Basis Review: This assessment reports on the SAP basis configuration settings against a set of industry best-practices.
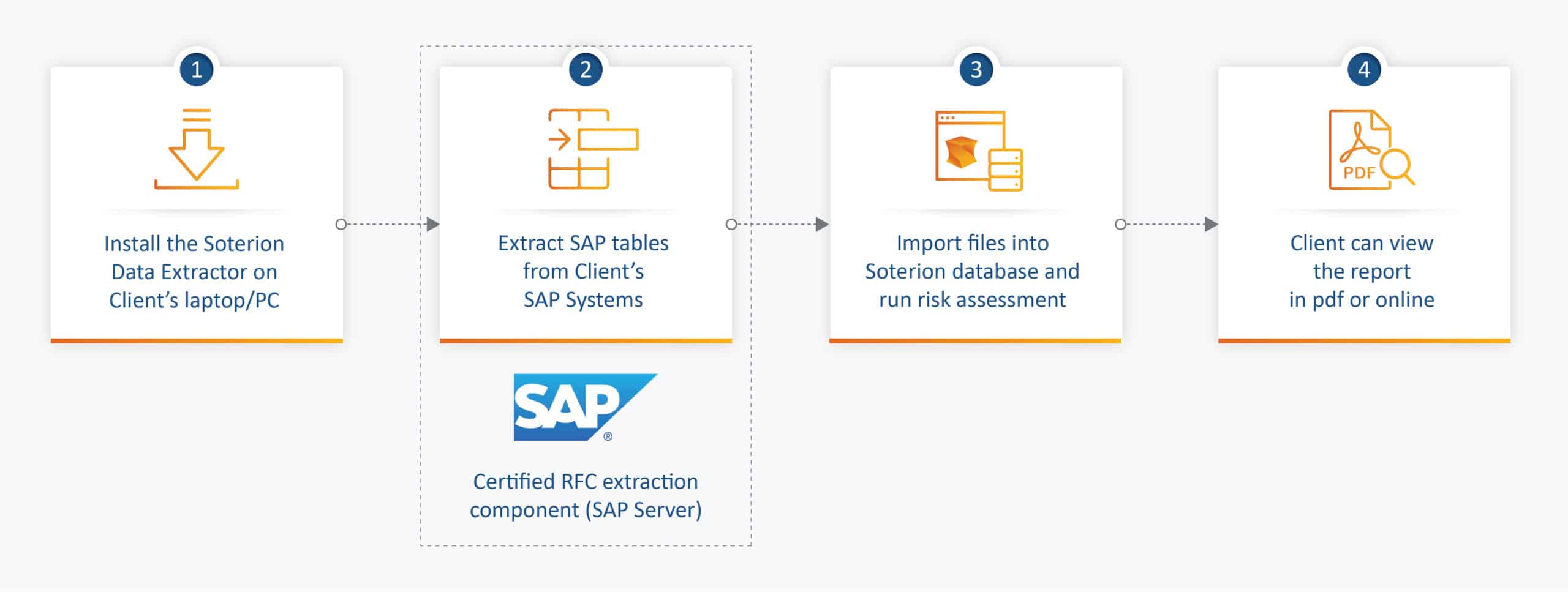
Soterion Access Risk Assessment Process
Viewing the Results of the Soterion Access Risk Assessment
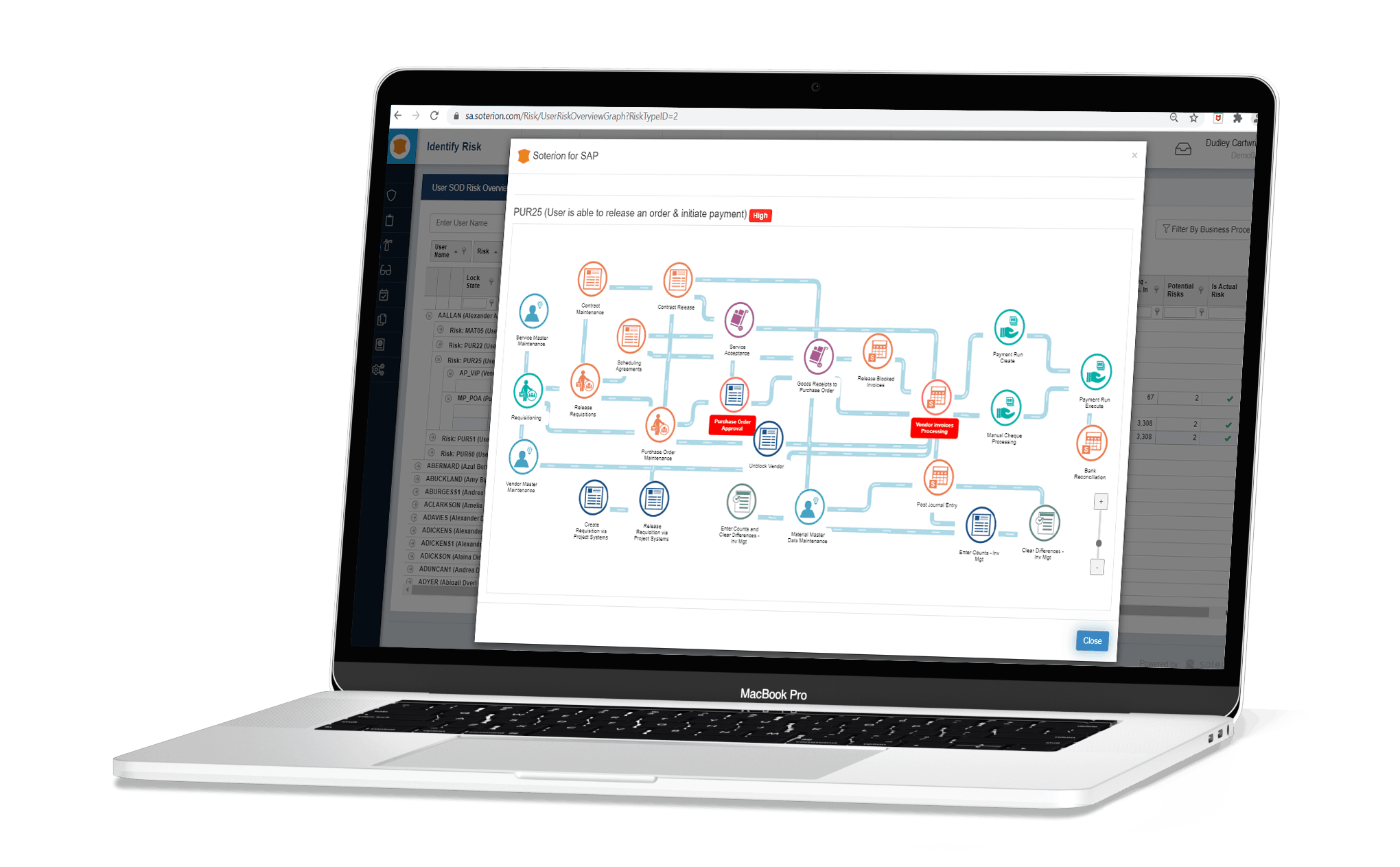
Soterion SOD Risk Detail – Business Friendly Reporting
One of the key advantages of a Soterion access risk assessment is that the results are displayed in the Soterion web application. This allows quicker analysis of the results and more effective remediation. Soterion will highlight the risks with the highest contribution, as well as flag the users and roles who are responsible for the majority of the access risk violations.
Soterion’s business-centric reporting capability will also illustrate each risk with supporting business process flow diagrams, thereby providing more context to the access risk and converting the technical GRC language into a business-friendly language to ensure better decision-making.
If your organisation is interested in having ad hoc assessments, please contact us – [email protected].